
Cybersecurity is a high-stakes game. Understanding the key differences between various types of cyber information is critical to a strong information security program. Organizations that take the time to understand the value of the digital assets they are protecting are more likely to leave the table as winners.
What Is At Stake?
What exactly is a digital asset? A digital asset is any form of proprietary content in electronic format. In today’s world, more and more companies maintain information in digital form. Some industries even have incentive programs (such as the Medicare and Medicaid Electronic Health Records (EHR) Incentive Programs) to facilitate the use of electronic records. The implications to these businesses and their clients could be catastrophic if those assets are lost, stolen, inappropriately manipulated, or subject to unauthorized access. Thus, it is critical for business owners to know both what digital assets they have in play and how to protect those assets.
Examples of high-value digital assets include:
- customer lists,
- ACH/wire transactions,
- payroll information,
- proprietary manufacturing processes, and
- product launch plans.
If something happens to these assets, the impact could go beyond the immediate financial hit to include a damaged reputation or a weaker competitive position.
3 Steps for Assessing Risks to Digital Assets
Protecting digital assets begins with a thorough risk assessment. This assessment should include the following key steps:
- Identify and prioritize digital assets. Consider the value of digital assets not only from your company’s perspective, but also from that of criminals, disgruntled employees, and competitors.
- Know where assets reside. Identify every place where digital assets are in use, at rest, or in transit – known as “states of data.” These “touchpoints” may include local workstations, portable devices, local networks, data centers, or email servers.
- Understand the risks of using third parties. Businesses that outsource asset management cannot offload the responsibility to sustain cybersecurity. They are responsible for knowing how those third parties protect those assets. Part of this knowledge may require a service organization control (SOC) report. A SOC report assesses the controls that service providers (e.g., data centers, software-as-a-service companies, etc.) have in place to maintain the integrity of their processes, systems, and data.
Strengthen Your Cybersecurity Posture
Working in the digital arena involves inherent risk. After assessing the value of the digital assets your business holds, you are prepared to take the next step in strengthening your cybersecurity: designing effective controls. Contact CRI’s cybersecurity team to discuss how your organization can uncover its risks and protect the assets that matter most.
Relevant insights
2024 Mid-Year Tax Planning Checklist for Business Owners

Why Do M&A Transactions Fail?

Boost Your Bottom Line by Understanding Your Internal Audit

When E-Commerce Sellers Would Benefit from Hiring an Accountant

Time Is Ticking on Business Valuation for Estate Planning

CECL: It’s Not Just About Financial Institutions

Five Tips for an Outstanding MD&A

Discover the Market Value of Your Business

Maximizing Estate and Gift Tax Strategies

Maximize Business Value with Solid Succession Planning

The Basics of Spousal Lifetime Access Trusts

Domain II – Ethics and Professionalism – An Ethics Update for...

Checklist: 8 Steps to Achieve Highly Productive Board Meetings

How to Develop a Cyberattack Recovery Plan

IRS Employee Tax Forms: A Checklist for Small Businesses

Natural Disasters Can Affect Your Financial Statement, Too

Tax Strategies for Special Needs Families

New IRS and Treasury Guidance Targets Basis Shifting Transactions in Partnerships

What Role Does Life Insurance Play in Estate Planning?

Employee Retention Credits: They Aren’t Dead for 2021 Yet!

Start From the T.O.P Down: Ways You Can Improve Your Organization’s...

U.S. Federal Tax Matters for Foreign Nationals

Deadline Approaching: All QuickBooks Desktop Required to Upgrade to Subscription Model...

Federal Tax Credits and Deductions for Family Caregivers

Act Now Before the TCJA Estate and Gift Tax Exclusion Sunsets

Easy Estate Planning Tips for Everyone

Understanding the Nuances: Traditional Non-Profits vs. Private Foundations

Excise Tax for Non-Profit Leaders: Understanding Penalties & Compliance

Succession Planning for Contractors: Necessary Strategies for a Smooth Transition

Crafting a Strategic and Compliant Grantmaking Plan for Private Foundations

FTC Issues Ban on Noncompete Clauses

S5:E3 – Local Government Opioid Settlement Accounting

Tax Planning and Compliance for Managing a Foundation

A Deep Dive into GASB Statement 103’s Financial Reporting Model Improvements

3 Governance Policies Every Business Should Have in Writing

Make Better Business Decisions with Financial Modeling

S5:E2 – Municipal Bond Underwriting: What’s It All About?

The Essential Role of Cost Reporting in Hospital Financial Management and...

Tennessee Assembly Passes Bill to Eliminate Franchise Tax Property Base

The Impact of an ESG Policy: How to Get Started

Strategic Financial Planning for Small Businesses in 2024

Harvesting Value: The Role of Bonus Depreciation in Enhancing Agricultural Investments

BSA/AML Model Validation: Understanding Expectations and Balancing Reality

At Long Last, GASB Approves Financial Reporting Model Improvements

To Lobby or Not to Lobby: Understanding Your Association’s Rights

Taxable Advertising or Nontaxable Sponsorship?

After the Standards: A Guide to Everything Else in a GASB...

Enhance Your Technology Tool Kit for Improved Productivity

Essential Governance Policies for Effective Associations

Avoid the Shock of a Surprise Tax Bill

It Figures Podcast: S5:E1 – CECL Lessons Learned and Opportunities Ahead

What Is Internal Audit and Can It Benefit Your Organization?

Don’t Jeopardize Your S Corporation Status

The Critical Role of SOC Reports in Nonprofit Operations

GASB Pronouncement Effective Dates: Post-GASB 95 Revisions

Treasury Urges Congress to Settle 831(b) Captives Issue

Federal Deposit Insurance Corporation Improvement Act (FDICIA) Requirements

Understanding the New Employee vs. Independent Contractor Classifications

Global Internal Audit Standards Resource

Inheritance Unplanned: The Unexpected Impact of Taxes on Families

How Should School Districts Report Charter Schools?

Resource: Identifying and Reporting Charter Schools as Component Units
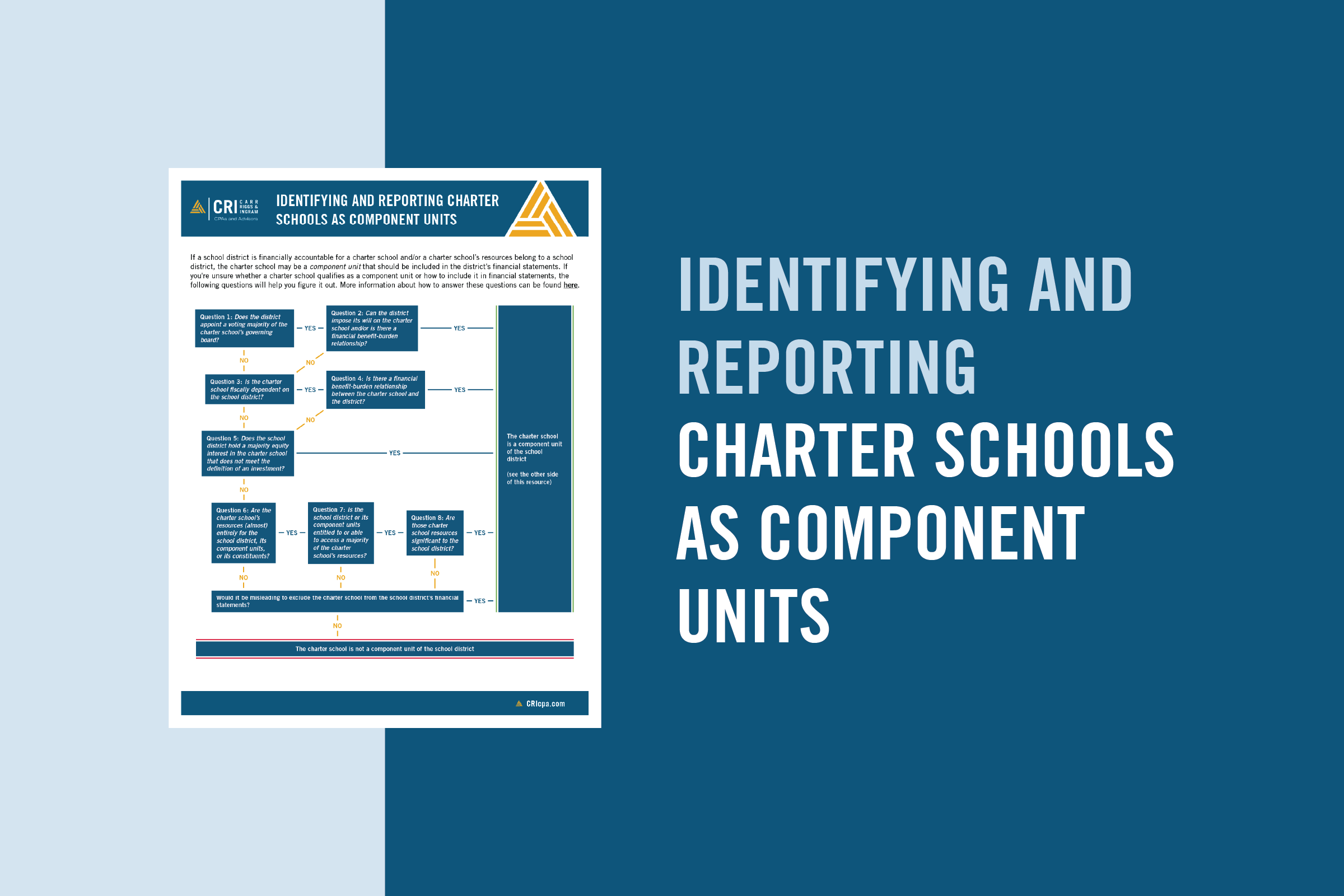
Are Charter Schools Component Units?

IRS Continues Pursuit of 831(b) Micro-captives in Tax Court Wins

Governmental Accounting & Auditing Omnibus

The Importance of Diversifying Your Customer Base

Discovering Your Business’ Value

Are Your Social Security Benefits Subject to IRS Taxation?

From Red Carpets to Tax Returns: The Versatile Roles of Accounting...

Pooled Income Funds Benefit Both Donor and Charity

Understanding the Implications of the House Committee’s Tax-Exempt Review

Introduction to the Global Internal Audit Standards

How Have Fraud Risks Changed?

5 Things to Remember About Substantiating Charitable Donations

Stay Vigilant to Reduce the Risk of Occupational Fraud

Crafting an Effective Nonprofit Document Retention Strategy

Ensuring Financial Integrity in Church Operations

Nine Questions About GASB Statement 102 on Risk Disclosures

State Tax Considerations for Insurance Companies

How to Be Prepared With a Business Continuity Plan

Real-Time Results: How Dashboards Can Help You Move Your Small Business...

Demystifying Deferrals: Illuminating the Intricacies of State and Local Government Accounting...

Key Discount Factors for 2023 Unpaid Losses in Insurance Companies

Fundamentals of Business Valuation: The Income Approach

Fundamentals of Business Valuation: The Market Approach

Optimizing Tax Benefits in Multi-Family Properties with Cost Segregation

Fundamentals of Business Valuation: The Asset Approach

2024 Cost of Living Adjustments Resource

IRS Issues Standard Mileage Rates for 2024

Loan Modifications Quick Reference Guide

Beneficial Ownership Reporting FAQs

New Beneficial Ownership Reporting Rules for Small Business

More Tips for Translating GASB Standards into English

Recent IRS Update: Postponement of Form 1099-K Reporting Threshold

Don’t Get Ready for Fiscal Year-End. Stay Ready.

Why Should You Consider a Sample Credit Card Agreement?
Key Insights for Employers on the Employee Retention Credit

Adapting to the IRS’s Electronic Filing Requirements

Help Your Business Finish Strong with These 10 Year-End Tasks

Faithful Finances: Crafting Credit Card Policies for Religious Organizations

Understanding the Hospitality Industry Audit Process

Unlocking the Value of Your Business, Part II: Post-Sale Considerations

Unlocking the Value of Your Business, Part I: Pre-Sale Considerations

5 Savvy Black Friday Shopping Tips to Put In Your Bag

EV Tax Credit Eligibility Flow Chart

Energy Tax Credits Table

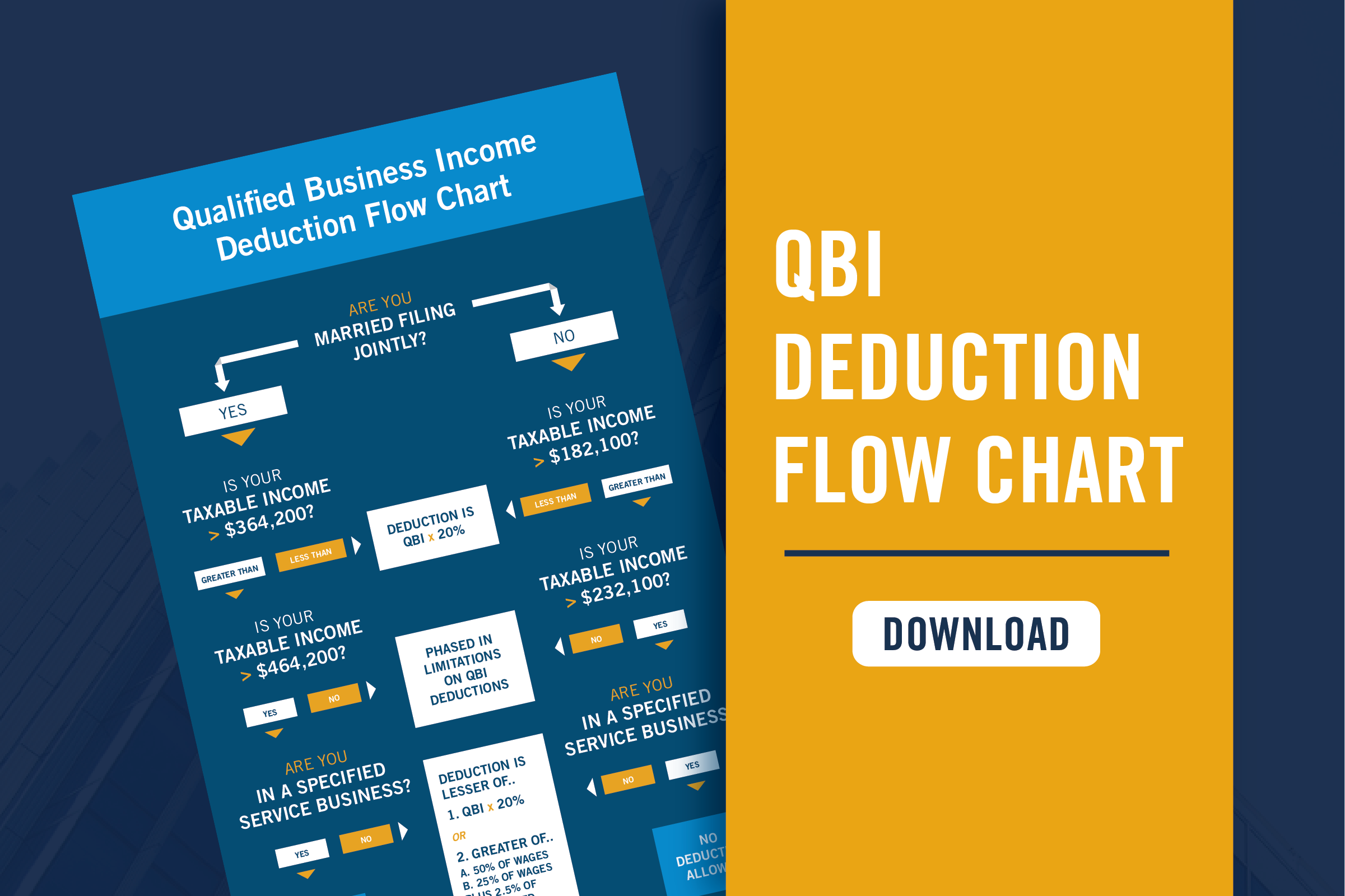
QBI Deduction Flow Chart
Tax Implications of Debt and Equity Financing

Ensuring Franchise Success through CPA Expertise
Tax Alert: IRS Releases 2024 Inflation Adjustment

Financial Institutions – Year-End Accounting and Risk Management Update

How Does Industry Affect Fraud Risk?

You, Too, Can Set Accounting Standards

Networking for a Cause: Utilizing LinkedIn for Nonprofit Success

Cost-Effective Fraud Protection

AR-C Section 70: When It’s Relevant and How to Apply It

The Role of Maquiladoras in Mexico and Global Manufacturing

Deferrals Study Guide

Understanding the New FASB Tax Disclosure Requirements
An SMB Leader’s Guide to Fraud Prevention

Balancing Faith and Finance: A Guide to Budgeting and Cash Management

Digital Privacy and the GDPR: Why You Should Pay Attention Now

Exploring the Benefits of Ministerial Compensation

Have You Completed These 5 Year-End Financial Planning Tasks?

The Pitfalls of Underbidding Projects

Strategies to Manage College Expenses for Multiple Children

Back to Square One: Six Questions About GASB’s Financial Reporting Model...

Security Implications of a Remote Work Environment

2023 Year-End Tax Planning for Individuals & Families: Strategize, Optimize, Maximize

2023 Year-End Tax Planning for Businesses: Strategize, Optimize, Maximize

The Evolving Landscape of Cryptocurrency Taxation

Step by Step: Stay Resilient with a Crisis Planning Checklist

IRS Alert: Update on ERC Claims

Understanding 1031 Exchange Transactions: A Strategic Move for Savvy Investors

Demystifying Deferrals: Technical Requirements & Resources

Demystifying Deferrals: Discussion Questions and Exercises

Unraveling Transfer Pricing Rules in Mexico

Contractors Can Remain Profitable in a Down Market

Florida Nursing Home Audit Requirements

Financial Resilience in the Face of Disasters for Older Adults

2023 GASB Update

Returning to Student Loan Payments: Ensuring Financial and Tax Compliance

Cybercrime and Religious Institutions: A Wake-Up Call for the Faithful

Five Steps to Elevate Self Pay Patient Collections in Medical Practices

5 Exercises to Rehabilitate Retirement Funds

Financial Impact of the Affordable Connectivity Program

Decoding Unrelated Business Income Tax

The Roadmap to a Successful Sale: Understanding the Phases of Selling...

With a Little Help From the GASB: Implementation Guides

Demystifying Deferrals: What They Are, What They Mean, and Why They...

Start Now to Comply with New Medicare Cost Report Rules

How to Properly Organize Your Tax Records

Form 990 Marketing: Spotlight Your Nonprofit’s Efforts and Achievements

Embedded Leases and Their Impact on Non-Profits
IRS Proposed Regulations on Micro-Captive Transactions

Deferrals from the Perspective of the User of Government Financial Statements
The Fine Line Between Nonprofit Lobbying and Advocacy

The Evolution of Healthcare Finance, Post-Pandemic

It Figures Podcast: S4:E19 – The Financial Data Transparency Act

Has Your Partnership or S Corporation Met the August 15 Notice...

Differentiating Between Independent Contractors and Employees

Transmittal 18: Critical Changes and Best Practices for Cost Reporting in...

New Rule for Catch-Up Contributions

It Figures Podcast: S4:E18 – Out with TDRs and in with...

After the Transaction: Look Here to Unlock Value in Post-Merger Integration

Building Your Ideal Captive Board

It Figures Podcast: S4:E17 – Medical Staffing Crisis

Drafting a Business Continuity Plan (BCP)

New Businesses Face Challenges When Proving Damages Based on Lost Profits

Beyond Compliance: Prioritizing Donor Data Privacy in the Non-Profit Sector

Planning for Possible Workforce Reductions

It Figures Podcast: S4:E16 – What Talent Really Wants

Tax Implications of Moving Abroad

Tax Concerns for Self-Employed Individuals

It Figures Podcast: S4:E15 – Current Trends in Mergers and Acquisitions

Deferred Outflows and Deferred Inflows of Resources in a Nutshell
Contractors Need To Juice Up Working Capital in Volatile Times

Checklist: Managing Your Loved One’s Estate

It Figures Podcast: S4:E14 – Demystifying Deferrals

Liquidity Risk for Community Banks

Litigation Support: Hire Forensic Accountants Earlier to Build a Stronger Case

How Secure Is Your Company Retirement Plan: Updates and New Rules...

Surviving Small Business Failure and Preparing for Future Success

Navigating Regulations in Government-Funded Projects

Introduction to the Global Internal Audit Standards 2023

Adapting to the New IRS Electronic Filing Requirement for Businesses

Six Common Nonprofit IRS Audit Triggers

Glossary of Accounting Terms

Using GASB Standards to Account for Opioid Settlements

Accounting 101: Debit and Credits

Liquidity Risk for Community Banks – Focusing on Fundamentals

It Figures Podcast: S4:E13 – Successful Transfer and Succession

It Figures Podcast: S4:E12 – Credit Risk Management in a Potential...

Standing in the Way of Construction Fraud

A Quality of Earnings Report Offers Key Insights for Parties Considering...

Navigating the Challenges of Global Supply Chain Disruptions

How to Reduce Your Hospital’s Compliance Risk with a Payroll Plan

It Figures Podcast: S4:E11 – Labor Market Changes and Effects

GARS: What It Is and Why You Should Be Using It

Sustainable Cost Management Strategies for Non-profits in Today’s Economic Challenges

It Figures Podcast: S4:E10 – A Guide to Employee and Workforce...

The Importance of Conducting a Valuation of Your Small Business

ORSA Requirements Help Insure a Comprehensive Understanding of Risks and Solvency

Revenue Recognition Implementation for Common Interest Realty Associations

Tribal Governments: Creating a Culture of Fraud Prevention

It Figures Podcast: S4:E9 – FDICIA Transition for Community Banks

Nonprofit & Governmental Healthcare Entities: Be Prepared to Justify Executive Pay

Why Filing a Tax Extension Can Be a Smart Move

How a Potential Non-Compete Clause Ban Stands to Impact Employers

It Figures Podcast: S4:E8 – The Who, What, Where, and Why...

Demystifying Deferrals

What You Need to Know About the Mississippi Pass-Through-Entity Election

Business Interruption: Planning Your Next Steps and Setting Expectations

It Figures Podcast: S4:E7 – Cost Segregation and Other Engineered Tax...

How Does Subscription Term Differ From Maximum Possible Term?

It Figures Podcast: S4:E6 – The Ins and Outs of Airbnb...

Inflation Is Redefining Private Equity’s Perception of Value

Tax Preparers: The Hero Your Company Needs!

Spring Cleaning Now Improves Business Performance All Year

It Figures Podcast: S4:E5 – SECURE 2.0 & The Impact of...

Implementing the New Leasing Standards for Contractor Financial Statements

CMS is Serious About Hospital Price Transparency

The Global Internal Audit Standards Are Coming; Is Your Organization Ready?

It Figures Podcast: S4:E4 – The Art and Science of a...

What Does the End of the Public Health Emergency Mean?

It Figures Podcast: S4:E3 SECURE 2.0 & The Impact on Individual...

It Figures Podcast: S4:E2 – Florida’s New Condominium Safety Law

What Is an Audit?

Gig Workers: What’s Up with Form 1099-K?

How to Avoid Mistakes in ESOP Valuations

Government Accounting Resources

K-2 – K-3 Exception Disclosure Comparison Chart

It Figures Podcast: S4:E1 – Adding Value To Your Internal Audit

Four Tips for Translating GASB Standards Into English

What Does the Consolidated Appropriations Act of 2022 Mean for Me?

Avoiding Improper Employee Retention Credit Claims

What To Consider When Creating a For-Profit Subsidiary

3 Reasons to Differentiate Between Controllable and Non-Controllable Costs

The New Lease Accounting Standard Is Here — Is Your Healthcare...

Spotlight on Controls and Internal Audit Departments
Did You Know…? A Guide to Governmental Accounting and Auditing Resources

The Importance of an Effective System of Internal Control

Building an Effective Nonprofit Audit Committee

2022 Partnership Instructions for Schedules K-2 and K-3

Lease Term vs. Maximum Possible Term
Nonprofit Considerations When Creating a Chart of Accounts

How the SEC Bridges the Divide between GAAP and Non-GAAP Financial...

Top 1099 Tips for Law Firms

The Ins and Outs of Physician Compensation Models

Business Entity Comparison

GASB Statement 94: Decoding P3s, SCAs, and APAs

Do You Qualify for the Home Gain Sale Exclusion?

Bonus Depreciation or Section 179: What’s The Right Choice for You?

Everyday Tax Return Items That Can Trigger an Audit

Getting From Here To There: New GASB Language for Effective Dates...

What Is The Roth IRA 5-Year Rule?

4 Benefits of a Government Audit Committee

Avoid These Tax Traps in Retirement

CRI Physician Services Planning for 2023

Financial Institutions Year-End Accounting & Auditing Update

Great News (Potentially) For 2022 Partnership Tax Return Filings

GASB Statement 100: Clarity for Accounting Changes and Error Corrections

ABLE Accounts: A valuable financial solution for people with disabilities

S1:E16 – When You Suspect Fraud: The Story of the Million...

Hop on the Omnibus: GASB Statement 99

Escalation Clause: Protect Your Bottom Line

Cost Segregation Studies: Opportunities for Contractors

Nursing Home Financial Reporting Bill in FL

It Figures Podcast: S3:E13 – An Inside Look at The GASB

Infrastructure Bill 101

All GASB Statements Are Not Created Equal

IRS Extends Federal Tax Filing Deadline for Hurricane Ian Victims in...

2022 Year-End Tax Planning for Businesses

2022 Year-End Tax Planning for Individuals & Families

The Infrastructure Investment and Jobs Act: Why to Expect a Marathon,...

Five Things to Know About the New Accounting For Paid Leave

Communicating with Your CPA: A How-To Guide

Understanding Your Accountant’s Language
It Figures Podcast: S3:E12 – Lease Accounting is for EVERYONE

Protecting Your Company Against Executive Impersonation Fraud

How to Implement Internal Controls in Small to Medium-Sized Nonprofits

It Figures Podcast: S3:E11 – CentraLease | GASB & FASB Lease...

Should Your HITRUST CSF Assessor Be a CPA Firm?

The 411 on Student Loan Forgiveness

GASB Update

CRI CECL Validation Services

Discount Rate Calculations for Lease Accounting

Key Takeaways From the Inflation Reduction Act of 2022

Taking Advantage of the Tax-Efficient Exit Strategy ESOPs Offer

Hunger Relief Efforts Can Yield Tax Benefit for Farmers

How Can Home Sellers Exclude Capital Gains Tax?

It Figures Podcast: S3:E10 – Balancing Acts: Managing Personal & Professional...

SBITAs: It’s Time to Boot Up

Understanding the Benefits of Engaging in a NIST CSF Assessment

Are Your Notes Turning Into Zombies?

Changes Reporting Gifts-in-Kind

The Arm’s Length Principle: The Rays of Transfer Pricing Adjustments

It Figures Podcast: S3:E9 – Shape Your Future: Internships

It Figures Podcast: S3:E8 – Understanding Inclusion & Diversity in the...

Retirement on the Horizon? Make Tax Planning a Priority

R&D Tax Credit Offers Tax Savings for the Cannabis Industry

Is It Time for a Reserve Analysis for Your Community Association?

In the Know: Pass Through Entity Tax (Georgia House Bill 149)

How to Use Real-Time Financial Data to Improve Your Cash Flow...

It’s Too Early for CECL Fatigue

Crypto Quick Reference Guide

Keeping the Business in Family Business

A High-Yield Investment Class: Novice to Proficient

Increase Your Chances of an Efficient Financial Statement Audit

Employee Versus Contractor: A Crucial Distinction for Every Organization

Bolster Cash Flow With a Cost Segregation Lookback Study

Cryptocurrency Fundamentals for Financial Institutions

Is Your Rental Real Estate a Business?

Solving the Hardship Withdrawal Program Administration Puzzle
Local Governments & The Final Rule: Coronavirus State and Local Fiscal...

It Figures Podcast: S3:E7 – The Transaction Timeline: The 5 Stages...

What is Section 1071, and Why is it Important for Your...

5 Tips for Lessening Stress with Nonprofit Audit Preparation

Knowing When to Claim Social Security

Coronavirus State and Local Fiscal Recovery Funds

Manufacturing Inventory Accuracy Counts

3 Benefits of Creating a Captive Insurance Company

It Figures Podcast: S3:E6 – Common ACFR Errors

Protect What Matters: Estate Planning in Uncertain Times

A Comparison of Education Tax Credits for 2023

Is it Time for a Business Valuation?

Give Your Small Business a Jolt of Efficiency with Cloud-Based Accounting

It Figures Podcast: S3:E5 – Heads up, Grant Professionals!

How Has COVID-19 Affected Business Valuations?

Reporting Computer-Security Incidents: Is your Community Bank ready?

What Does a Cash Balance Plan Mean for You?

The Name’s Bond, Government Bond

Setting Nonprofit Executive Compensation

Promises to Give: Not-for-Profit Accounting Primer

Does Working Remotely During the Pandemic Mean You Owe More Income...

Still Confused About Whether to Deduct That Business Meal?

New HITRUST Assessments Give Companies More Options for Security Reporting
ICBA Live 2022 Conference Recap

You Could Owe “Nanny Taxes” Even If You Don’t Have Kids

Nonprofit Board Review of Form 990

Managing ESG Risks in the Oil and Gas Industry

Charitable Lead Trust vs. Charitable Remainder Trust: A Comparison
It Figures Podcast: S3:E4 – SSAE No. 21 | Direct Examination...

Going Concern Issues for Nonprofits

Improve Medical Practice Productivity with Non-Physician Providers

Five Internal Controls to Prevent Fraud in Nonprofits

Safeguard Your Assets During a Divorce — Before You Get Married

Differences in Public Charities and Private Foundations

It Figures Podcast: S3:E3 – Panic! At the IRS Disco

Report Fundraising Events on Form 990

3 Grant Writing Tips to Help Not-For-Profit Organizations

Health Savings Accounts Offer Big Tax Benefits Now and in Retirement

Short on Cash? Gift-in-Kind Donations Can Also Help Support Charities

Estate Planning FAQ

Transfer Your Wealth Using a Dynasty Trust

Two Types of Charitable Trusts You Should Know About

New Guidance on Gifts In-Kind for Non-Profit Entities

It Figures Podcast: S3:E2 – Count Yourself in to a Career...

Captive Insurance Taxation

Top 5 Priorities for Small and Mid-Sized Organizations in 2022
A Look at Internal Controls and Processes for Evaluating Vendors

Getting the Most Out of Your Remote Audit

Moving to a New State? Don’t Make These Tax Mistakes

Coronavirus Relief Funds – Getting Ready for Your Single Audit

Does Your Organization Need an Internal Audit?

What a Single Audit Means for Your Organization

Straddling the Fence: Should You Co-Source or Outsource Your Internal Audit?

COVID-19 Funding Best Practices, Accounting Treatment, and Single Audit Implications

Cybersecurity Trend to Watch in 2021: Cyber Supply Chain Risk

Outsourced Accounting Reference Guide: How Collaborating Can Help You Reach Your...

Fiduciary Matters: How to Be the Best Trustee for Your Organization’s...

It’s a Marathon, Not a Sprint: Going the Distance for Outsourced...

2021 Year-End Tax Planning for Businesses: Strategize, Optimize, Maximize

2021 Year-End Tax Planning for Individuals & Families: Strategize, Optimize, Maximize

Conference Recap – AICPA 2021 National Conference on Banks and Savings...

CECL: It’s Getting WARM in Here Webinar

It Figures Podcast: S2:E17 – Beers, Beets, Governmental Accounting

Credit Memorandum Best Practices and “The 5 C’s”

It Figures Podcast: S2:E16 – Just You, Me, & the ERC.

Keeper of the Vault: A Business Owner’s Guide to Cybersecurity

Federal American Rescue Plan Act of 2021 (ARPA)

COVID-19 Quick Hits: American Rescue Plan Act Overview

It Figures Podcast: S2:E15 – Insurance Compliance and Regulatory Examination Process...

Risky Business: Comparing Risk Levels of MRBs

Employee Retention Credit Information Sheet

IRS Income Tax Forms: A Checklist for Small Businesses

Digital Transformation Starts With Process, Not Technology
What’s New from GASB: An Update on the Latest Standards

Homeowner Assistance Fund – What Tribes and Applicants Need to Know

CECL: It’s Getting WARM in Here

Homeowner Assistance Fund – You Don’t Know the HAF of it!

Questions About the Employee Retention Credit? We’ve Got Answers.

American Rescue Plan for Governments: The Resources Available

Potential Proposals on the Horizon: It’s Time to Prepare Your Estate...

Strategic Use of ARP Government Funds for Long-Term Success

IRS Notice Provides Guidance to Employee Retention Credit and the Paycheck...

Time to Pivot? How Your CPA Can Help You Adapt to...

Compliance Management System (CMS) – A Refresher

The Basics of Grantor Retained Annuity Trusts

Tax Considerations for Buyers Contemplating Mergers & Acquisitions

Taking a Fresh Look at Bankruptcy

IRS Clarifies Temporary 100% Deduction for Restaurant-Purchased Meals

Hired Any Recently Unemployed Workers? Let Them Know About New Exclusion...

Strategic Decision Making: Are You Taking Advantage of the Newly Expanded...

Rate Reform – Why is LIBOR Going Away, and What Will...

Clear Vision: Moving Your Business Forward with Confidence

Five Overlooked Tax Breaks for Contractors and Manufacturers

How Contractors Can Bridge the Age Gap

Why Profits Do Not Always Lead to a Positive Cash Flow...

IRS Provides Guidance on Cafeteria Plan Balance Carryovers

Updates to the AICPA’s SAS No. 134 through SAS No. 140

SSAE No. 21 – Direct Examination Engagements

Not-For-Profit Revenue Recognition

Now or Later? Weighing 15-year Depreciation vs. 100% Bonus Depreciation for...

How to Spot Three Common Tax Scams

Insurance Companies and the IRS: What’s on the Horizon?

The Anti-Money Laundering Act of 2020: An Overview

Federal Audit Clearinghouse Extended Submission Dates FAQs

When Can You Deduct Data Breach Costs?

Boost Your Cash Flow with Net Operating Loss Carrybacks
What’s Next for Hemp-Related Businesses?

Should You Convert Traditional IRA to Roth? Think Twice.

Making Intrafamily Loans with Intentionally Defective Grantor Trusts

The IRA: A Solid Estate Planning Tool in Times of Uncertainty

How MaaS Is Revolutionizing Manufacturing

Export Tax Incentives for Manufacturers

Meals & Entertainment

Credit Risk Management in an Unpredictable Environment

Insurance Companies and the IRS: A Downward Trend in Examinations

Exempt Organizations: IRS Issues Final Rules on 21% Excise Tax on...

Coloring Inside the Lines of Nonprofit Governance

How Does Your Industry Affect Your Cybersecurity Risk?

USDA Issues Final Rules on Hemp Production

Not-So-Safe Harbor? Navigating the QBI Rules for Rental Real Estate Businesses

Disasters Never Rest, Take Time to Plan for Recovery

Yes, Operational Planning Is Still Important

Does Your Home Office Qualify for a Tax Deduction?

Shutting Down a Business? Updated Resources Available from IRS

Lending Money to Family? Be Sure to Stay on the Right...

Updates to the Long-Anticipated Compliance Supplement Addendum

Preparing for Third-Party Payer Audits

Five Ways to Make Invoice Processing More Effective

Is It Time for Cloud Accounting?

Watching the Horizon: Do You Have the Data You Need to...

Key Factors that Drive Reimbursement in the PDPM Model

What’s Behind the Hype About Donor-Advised Funds?

Businesses Face Challenges When Expanding Their Remote Workforce

Helpful Tips for Completing Medicare Cost Reports

Technology Innovations Impacting the Insurance Industry

10 Anti-Fraud Recommendations for Community Associations

Don’t Sleep on CECL

Social Engineering Attacks: Considerations for SMBs

Smarter Giving: Four Things to Know When Considering Charitable Contributions

How Important is Compliance with Government Regulations to a Firm’s Accounting...

Contractors Should Take A Closer Look at Site-Level Profitability

Assembling an Effective Financial Team

PRF Requirements Summary

Prepare, Recover, Emerge Stronger: A Roadmap for Financial Perseverance in Times...

CARES Act and Provider Relief Fund Single Audit

Back to Profitability: How Small Businesses Can Emerge Stronger from Crisis

Virtual Meetings: Tips for Choosing the Right Technology and Conducting a...

Calculating Your Business Interruption Loss

Maintaining Financial Controls in a Disrupted, Remote-Work Environment

How to Increase Your Chances of a Successful Financial Statement Audit

Healthcare Organizations: Are You Ready for New Revenue Recognition Rules?

Business Interruption Losses: Making an Insurance Claim

Cybersecurity Tips for Working From Home

Understanding the Basics of Business Interruption Claims

Stabilizing Your Business: Improvise, Adapt, Overcome

Government Entities: Plan, Protect, Adapt, Overcome

Make the Most Out of Your P&L

How to Arrange a Medical Practice Buy-Sell Agreement that Minimizes Disputes

Is a Captive Right for Your Organization?

Forensic Audits vs. Annual Audits: Taking a Proactive Approach to Protecting...

Automated Bank Reconciliation: An Instant Analysis for Your Business

Unique Compliance Aspects of Risk Retention Groups

Improve Manufacturing Company Profitability

What’s Your Company’s Cash Flow?

Record Retention Schedule

Preparing for a Single Audit: Understanding the Requirements

A Grant Overview

Understanding Your Responsibilities Within Service Organizations

When Does a Hobby Become a Business?

Make Digital Assets Part of Your Estate Plan
What You Need to Know About the Home Office Deduction

Keeping a Close Eye on Medicare Fraud

Privacy Policies and Data Security Keep Contributions Flowing for Not-for-Profit Organizations

8 Action Steps for Avoiding Nonprofit Online Presence Tax Traps

Impressing Donors with Nonprofit Financial Information

Two Types of Government Termination Benefits

The Growing Threat of Cyberattacks in Manufacturing and How to Prevent...

Is Your Manufacturing Business Ready for the New Revenue Recognition Standard?

A Blueprint for Nonprofit Revenue Recognition Implementation

Qualified Opportunity Zones: A Resource Guide

Living in a Post-Wayfair World

Citizen Centric Governmental Reporting

Municipal Bond Arbitrage, Billy Ray Valentine, and What They Have in...

Disaster Recovery: Protect Your Assets With the Right Insurance

Don’t Let These 7 Tax Terms Scare You

Three Actions to Help Improve Your Collections Process

Acknowledgments of Nonprofit Donations

UPMIFA – That’s Not a Text

Balance Sheet Reconciliations: Focus on Internal Controls

Charitable Donation Documentation: 6 Answers to Know

Closing a Nonprofit Organization

For Strong Data Security, Give Your Employees Some Backup
Transfer Pricing and Not-For-Profits (UBIT)

Why Fair Value is Becoming a Popular “Celebrity” in the Accounting...

Bracing for Disaster? Prepare to Deduct Casualty Losses

Use a Governmental Performance Audit to See If You Measure Up

Risk Management: Avoiding Crisis & Staying Afloat

Using Internal Controls to Keep a Record of Your Inventory: Storing...

4 Things the IRS Looks for in a Federal Tax-Exempt Application

Using Nonprofit Financial Statements for Future Planning

Implementing Nonprofit ERM Strategies

3 Common Questions & Answers: Nonprofit Audit Committee

Love, Marriage, and Uncle Sam: How Getting Married Affects Your Taxes

7 Benefits of Outsourcing a Not-for-Profit Organization’s Essential Bookkeeping and Payroll...

How the Internet Mystifies the Taxability of Qualified Sponsorship Payments

Tax Planning Reasons to Potentially Establish a Private Foundation

Manufacturing Product Costing

Financial Statement Preparation: 4 Steps to Power Up Business Performance Tracking

What to Consider When Deciding Between a Calendar Year and a...

Best Practices for Nonprofit Volunteer Management

Captive Insurance Overview: Healthcare Provider Industry Highlights

Small Business Compliance: Are You Sticking to the Law?

Five Steps to Prepare a Disaster Plan for Your Business

Restructuring Organizations Through Tax-Free Business Splits

Taking a Bite Out of Payroll Taxes

How to Protect Yourself from Tax Identity Theft

Anti-Money Laundering (AML) Implications of Human Trafficking

How Manufacturers Should Account for Excess Capacity

3 Questions to Find the Balance of a Seasonal Product Cycle

Opportunity Zones: Open for Business

What is a Governmental Component Unit?

4 Steps on the Path to Timely Payments

Understanding the Management’s Discussion and Analysis (MD&A) Disclosure

The Evolution of the Bank Secrecy Act

Business Valuation Can Avoid a Merry-Go-Round During Divorce Proceedings

The Continued Importance of Risk Assessment for Financial Institutions
The Bank Secrecy Act/Anti-Money Laundering (BSA/AML) Audit Revisited

Opportunity Zones are Knocking: Should You Answer?

It’s Time to Review and Update Your Partnership Agreement
Using Internal Controls to Keep a Record of Your Inventory: Costing...

Clear Reliable Insights: GASB 87

How to Manage Supplier Costs and Keep Your Business Balanced

3 Ways Public Companies Can Iron Out SEC Audit Processes

Travel Guide for Your Start-Up’s Journey to Success

How to Become the Boss of Your Digital Assets

Steering Clear of Bookkeeper Liability Hazards

Four Must-Have Features When Selecting an Auditor

Will Your Cybersecurity Defense System Protect Your Organization?

“Yours, Mine, or Ours?”: Identifying and Valuing Marital Property

One Taxing Situation: South Dakota vs. Wayfair, Inc

IRS Correspondence Letter: Your New Pen Pal the IRS

Is Your Bank’s Audit Committee Reaching the Summit of their Potential?

Will Your Cost Segregation Methodology Hold Water With the IRS?

Understanding Terms Found in Common Business Interruption Policies

Business Interruption Claims Can Prevent the Unexpected

How the SEC Bridges the Divide Between GAAP and Non-GAAP Financial...

An Origin Story About Captives

Sail Smoothly Through Those Saving or Shredding Decisions

The Opportunities of Effective Risk Management

How the Pooling Method Can Help Bring Your Property Value to...

Why Strong Internal Controls Are Necessary for a Healthy Business

Avoid the Punch of Ransomware

4 Business Seasons When You Should Consider a Virtual CFO or...

Whaling Cyberattacks: What You Need to Know

How to Maximize Business Sale and Successfully Exit

4 Simple Solutions to Improve Financial Reporting Timeliness without Breaking the...

8 Steps for Cleaning Up a Tax Return Identity Theft Train...

Unearthing Occupational Fraud in Your Business

Life Insurance Tax Strategies: Maximizing this Multi-Use Tool

Watch for These 3 Signs of Employee Fraud

Join Our Conversation
Subscribe to our e-communications to receive the latest accounting and advisory news and updates impacting you and your business.