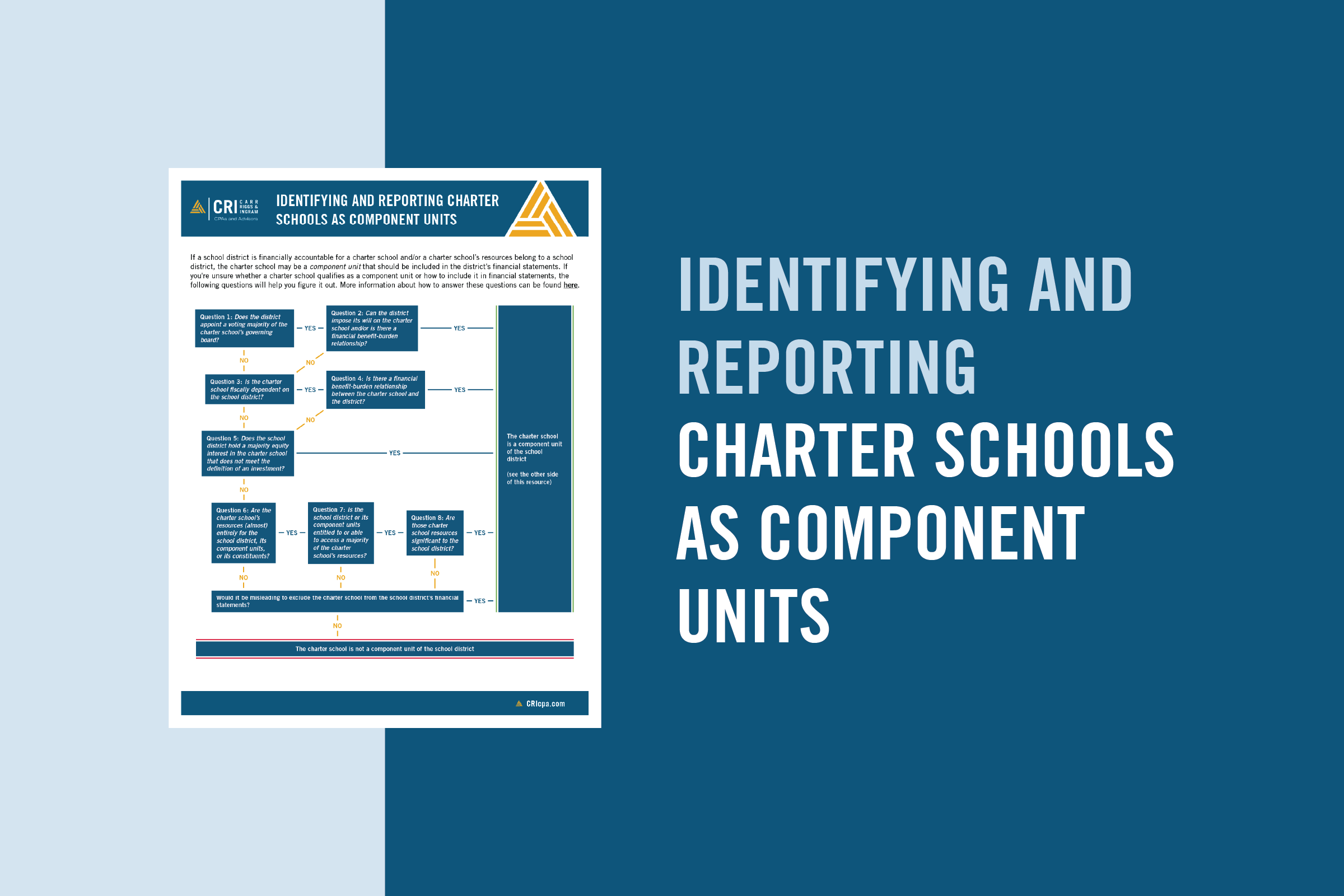
Reporting Computer-Security Incidents: Is your Community Bank ready?
Mar 21, 2022
It's not a secret that banks have a significant amount of personal information, and many people want that information for malicious purposes. As cybersecurity and computer-related crimes continue to increase, the Federal banking regulators have taken notice and are now requiring additional reporting. The regulators want to be made aware of these incidents to best help the affected banking organization, become familiar with patterns of computer-related crime, and inform other banks of threats they see throughout the banking system.
In November, the Federal Deposit Insurance Corporation (FDIC), the Board of Governors of the Federal Reserve System (Board), and the Office of the Comptroller of the Currency (OCC), issued Financial Institution Letter (FIL)-74-2021. Effective April 1, 2022, with a compliance date of May 1, 2022, once a notification incident has occurred, banking organizations are required to notify their primary Federal regulator as soon as possible and no later than 36 hours of the incident. The FIL states the Federal regulators will have an appropriate agency-designated point of contact through email, telephone, or other similar methods that the agency may prescribe. A bank service provider is to notify a bank-designated contact at each of its customer banking organizations as soon as possible once the bank service provider determines it has experienced a computer-security incident.
The rule defines a computer-security incident as an occurrence that:
- Results in actual or potential harm to the confidentiality, integrity, or availability of an information system or the information that the system processes, stores, or transmits; or
- Constitutes a violation or imminent threat of violating security policies, security procedures, or acceptable use policies.
The rule further defines a notification incident as a computer-security incident that a banking organization believes in good faith could materially disrupt, degrade, or impair—
- The ability of the banking organization to carry out banking operations, activities, processes, or deliver banking products or processes, or deliver banking products and services to a material portion of its customer base, in the ordinary course of business.
- Any business line of a banking organization—including associated operations, services, functions, and support—and would result in a material loss of revenue, profit, or franchise value; or
- Those operations of a banking organization, including associated services, functions, and support, as applicable, the failure or discontinuance of which would pose a threat to the financial stability of the United States.
The rules provide a non-exhaustive list of example incidents generally considered "notification incidents."
- Large-scale distributed denial of service attacks that disrupt customer account access for an extended period (e.g., more than 4 hours);
- A bank service provider that a banking organization uses for its core banking platform to operate business applications is experiencing widespread system outages, and recovery time is undeterminable;
- A failed system upgrade or change that results in widespread user outages for customers and banking organization employees;
- An unrecoverable system failure that results in activation of a banking organization's business continuity or disaster recovery plan;
- A computer hacking incident that disables banking operations for an extended period of time;
- Malware on a banking organization's network that poses an imminent threat to the banking organization's core business lines or critical operations or that requires the banking organization to disengage any compromised products or information systems that support the banking organization's core business lines or critical operations from internet-based network connections; and
- A ransom malware attack that encrypts a core banking system or backup data.
What does this mean for your banking organization?
First, if not already established, ensure that you have one point person responsible for receiving any notification of incidents in your agreement with your core service provider. This should be reviewed and updated annually as you conduct vendor management reviews.
Second, update policies and procedures to define, according to the FIL rule, what a notification incident is and the process for communicating that incident to your federal regulators. As turnover takes place with agencies, ensure you have the most recent contact documented in policy/procedures or wherever you maintain contact information for your federal regulator.
Third, consider conducting a tabletop exercise annually. This could be done as part of your business continuity plan process walkthrough, ensuring the key members of management know how to communicate incidents under this rule accordingly.
Finally, contact CRI. We have a broad knowledge of banking regulations and cyber security. We can help you draft the proper policy and procedures to follow and assist in communicating with your regulator when an incident requiring notification occurs. We have assisted clients who have been victims of computer-security crimes and can help you and your banking organization in its time of need.