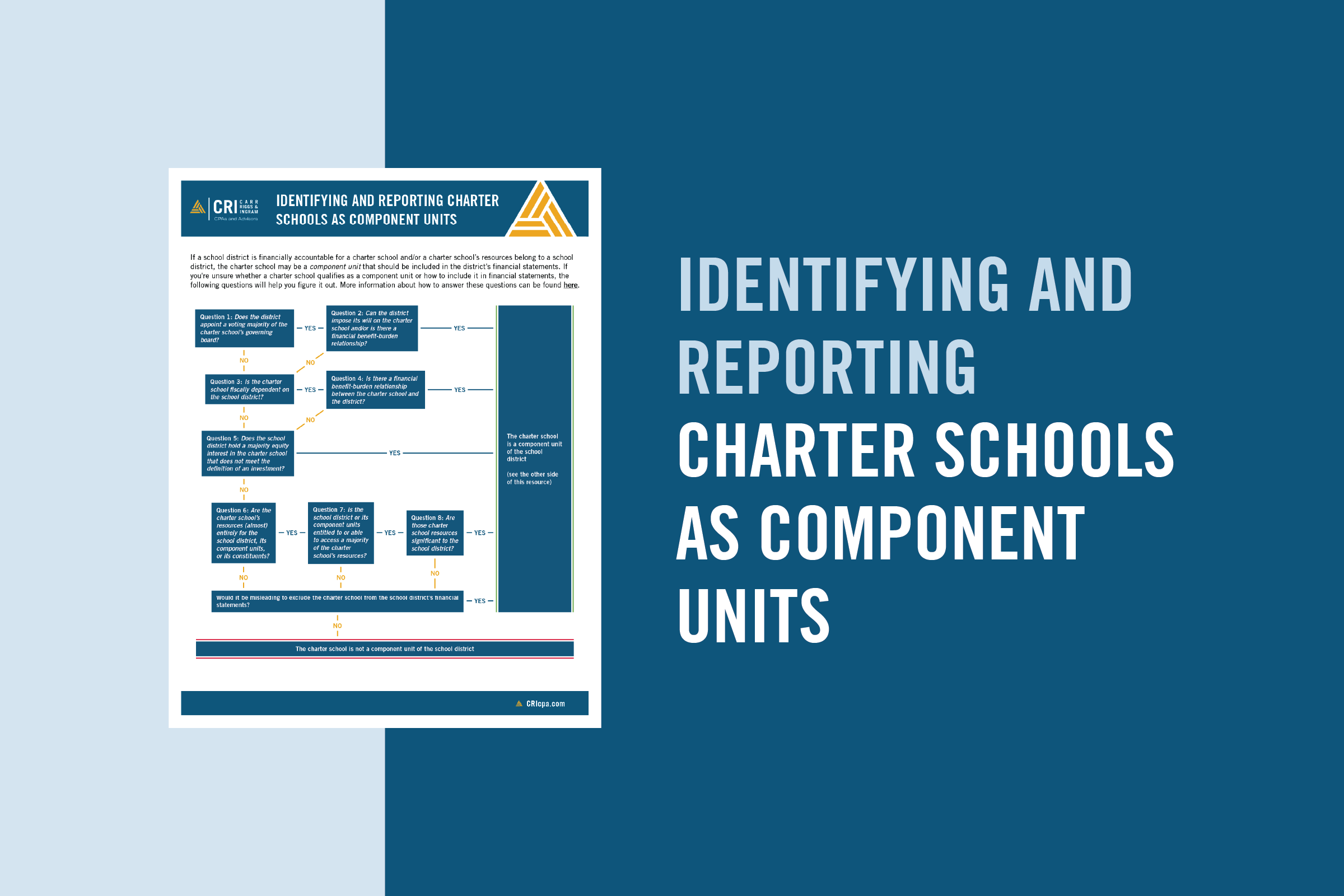
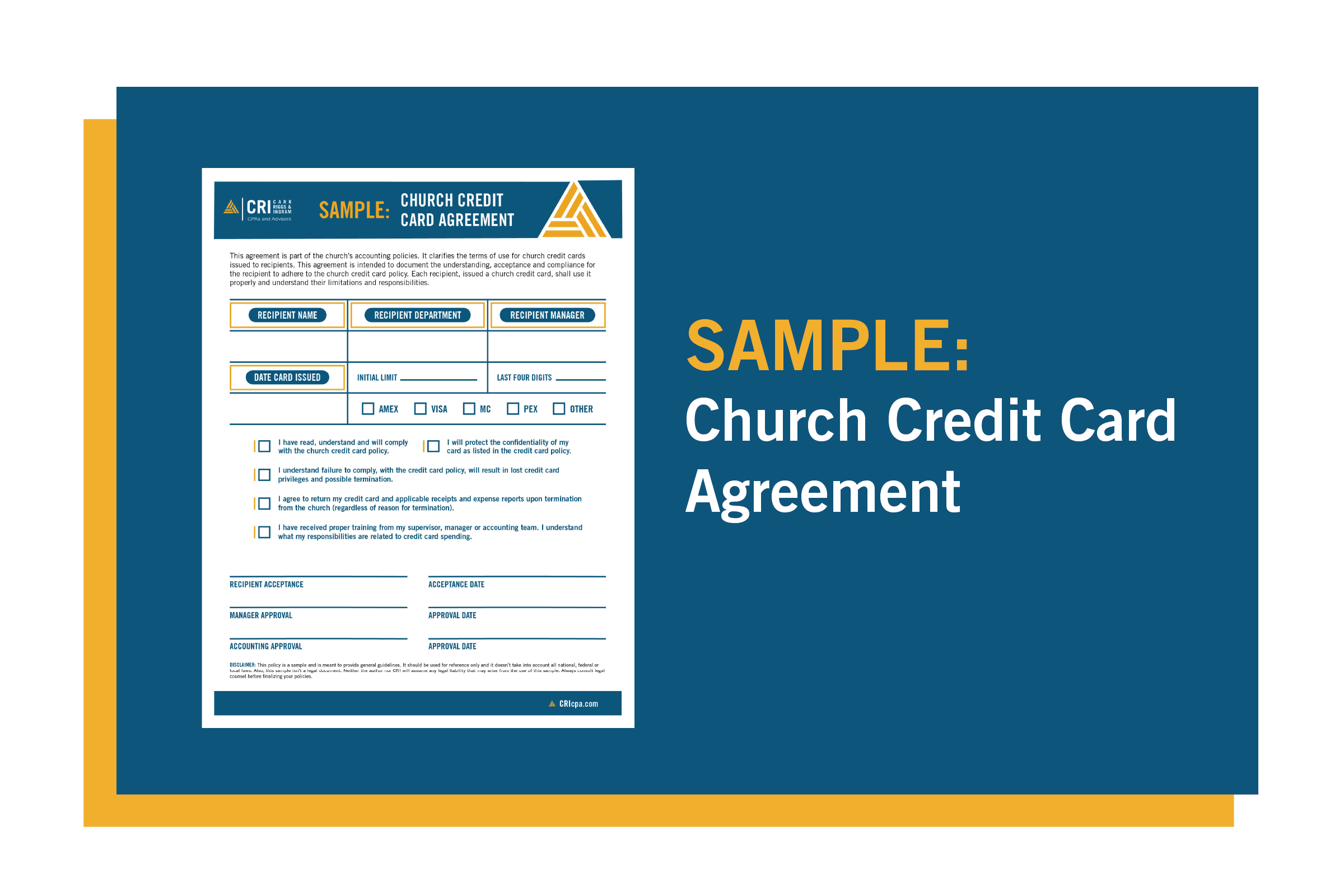
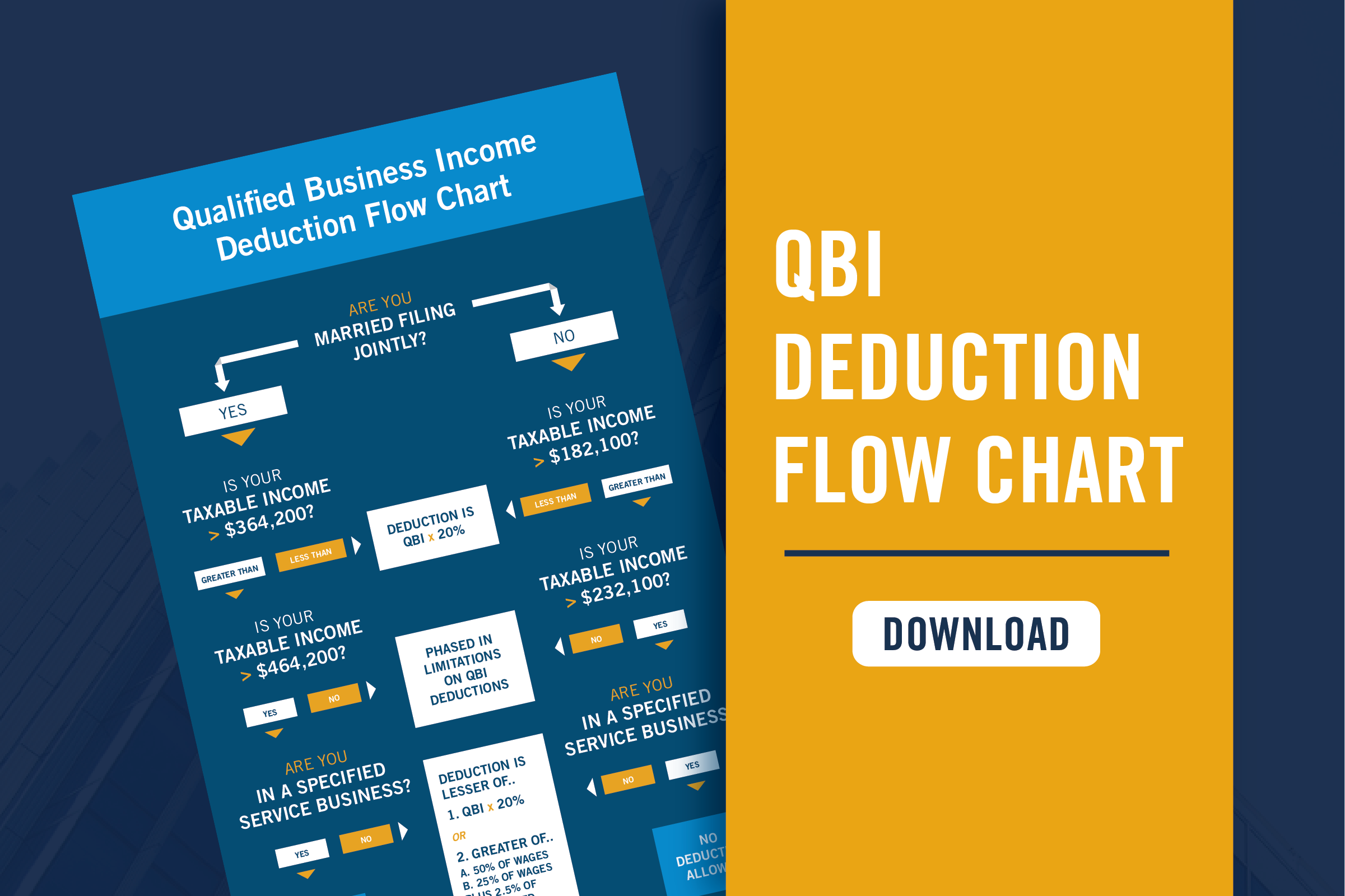
Understanding the Benefits of Engaging in a NIST CSF Assessment
Aug 15, 2022
A cyber breach can have potentially devastating effects on a company. It can erode public trust, cause millions of dollars in losses, and even lead to fines and lawsuits. In order to help organizations improve cybersecurity, the National Institute of Standards and Technology (NIST) released its Cybersecurity Framework (CSF), which provides several guidelines related to managing and reducing risks.
Independent NIST CSF assessments completed by a CRI Certified Information Systems Security Professional (CISSP) use five functions and the controls around them to provide insight on the specific cybersecurity needs of organizations.
Identify
First, if there is some sort of cyber breach, it is paramount to have a certain level of controls in place. For instance, a company may have some type of monitoring system in place to detect intrusions. Alternatively, there may be a threat detection metric that reads logs in order to flag specific file changes. Having the tools in place to identify breaches when they occur is a key aspect of mitigating risk and damage.
Protect
Each client has different security needs. A smaller local business may require a simpler protection plan, whereas something more complex may be necessary for a large multinational corporation that deals with sensitive information. NIST CSF assessments performed by CRI assessors aim to ensure organizations have as much protection as possible, which starts with the evaluation of a number of different aspects of a protection plan. It is crucial to ensure that the firewall is working and properly monitored. Employees need to be trained and understand how to react if a breach occurs. Without having measures like this in place, a company can put itself—and clients—at high risk.
Detect
After making sure that breach controls are in place, the next step is to detect if one has occurred. There are distinct ways to tell. For example, if a computer has been hit with ransomware, the user may see the dreaded skull and crossbones graphic appear on their screen. However, that means it is too late to do something. Detecting a breach, or an attempted breach, is a crucial step towards mitigating or preventing a cyber attack. A combination of technological and people-based controls are needed when it comes to detecting breaches. Typically, companies will have a unique set of needs based on their size and the complexity of their operations.
Respond
Once a breach is detected, it’s time to respond as quickly as possible. If a breach occurs to a specific network, the issue must be isolated to prevent spreading. Additionally, the response isn’t solely limited to the IT side of things. There also needs to be a proper response in regards to communications. With so much sensitive information at risk, ensuring that these policies are in place make certain that no data is divulged to the general public.
Recover
After responding to the impact of a breach, it’s now time for the recovery process. This is the final stage when evaluating a company’s capabilities for mitigating damage from a breach. There needs to be procedures and policies in place that aim to fix what was affected by the incident. For instance, recovering from a ransomware attack requires that specific backup processes are followed.
If your organization is interested in engaging in an independent NIST CSF assessment, contact your CRI professional for more information on how to begin the process.