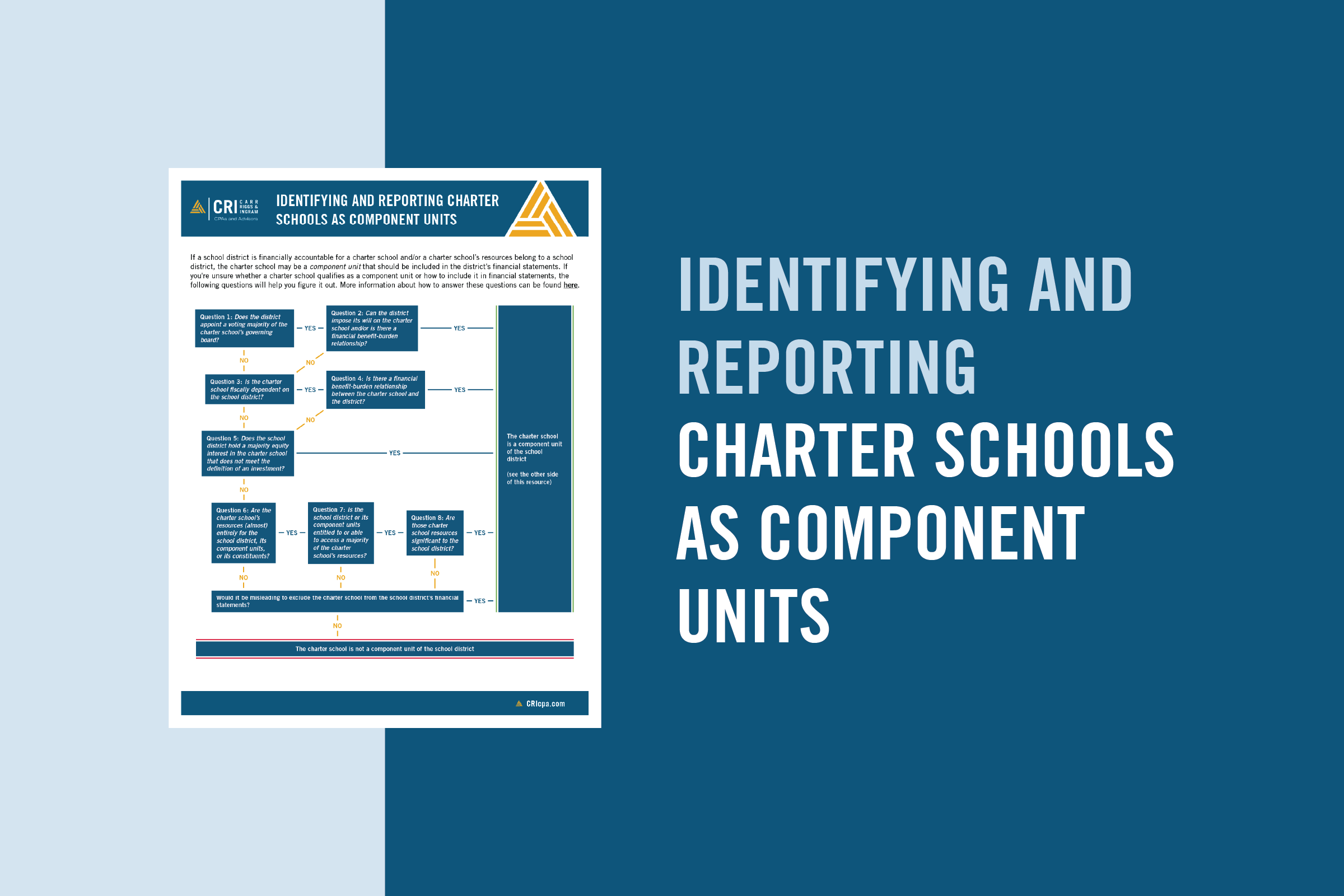
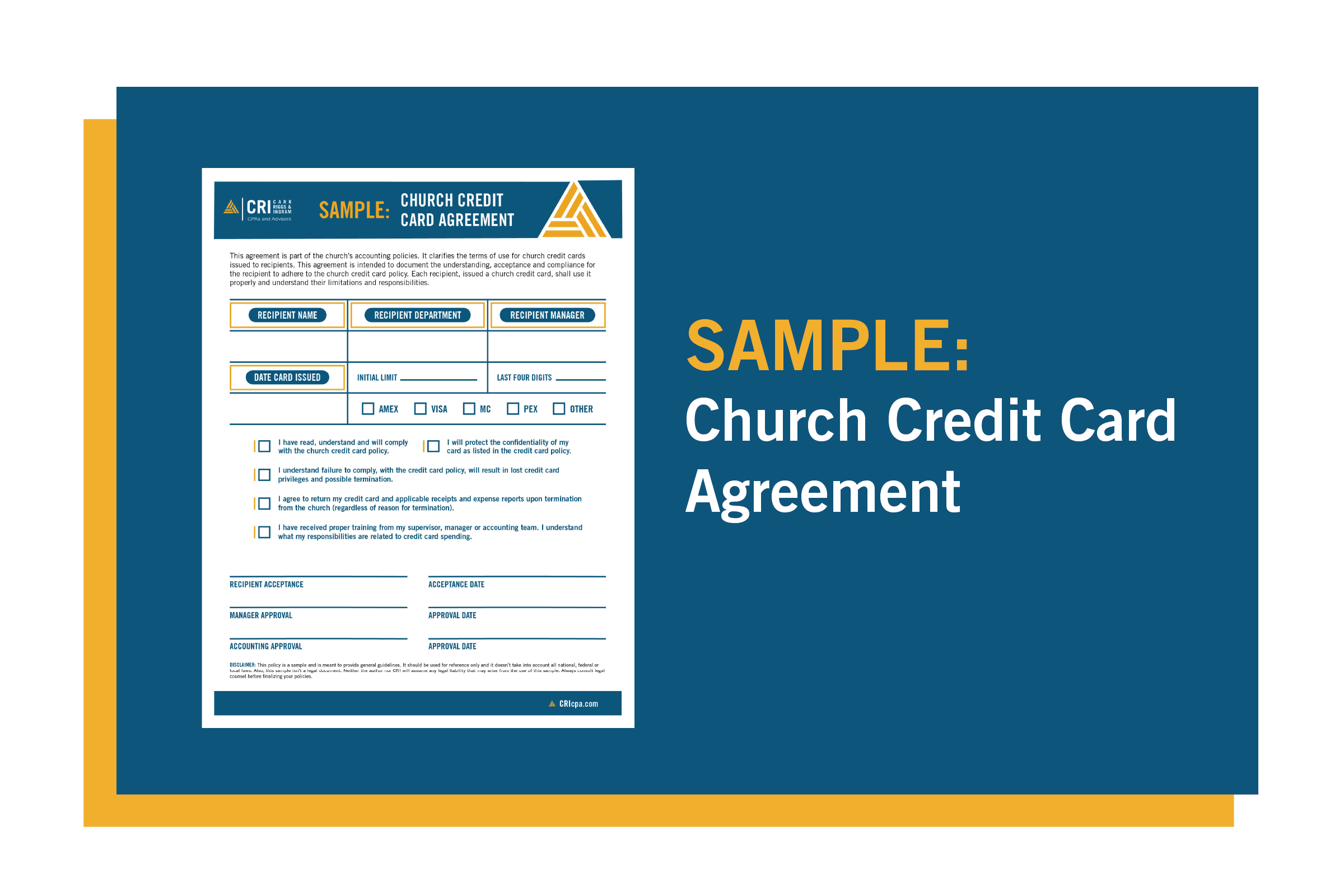
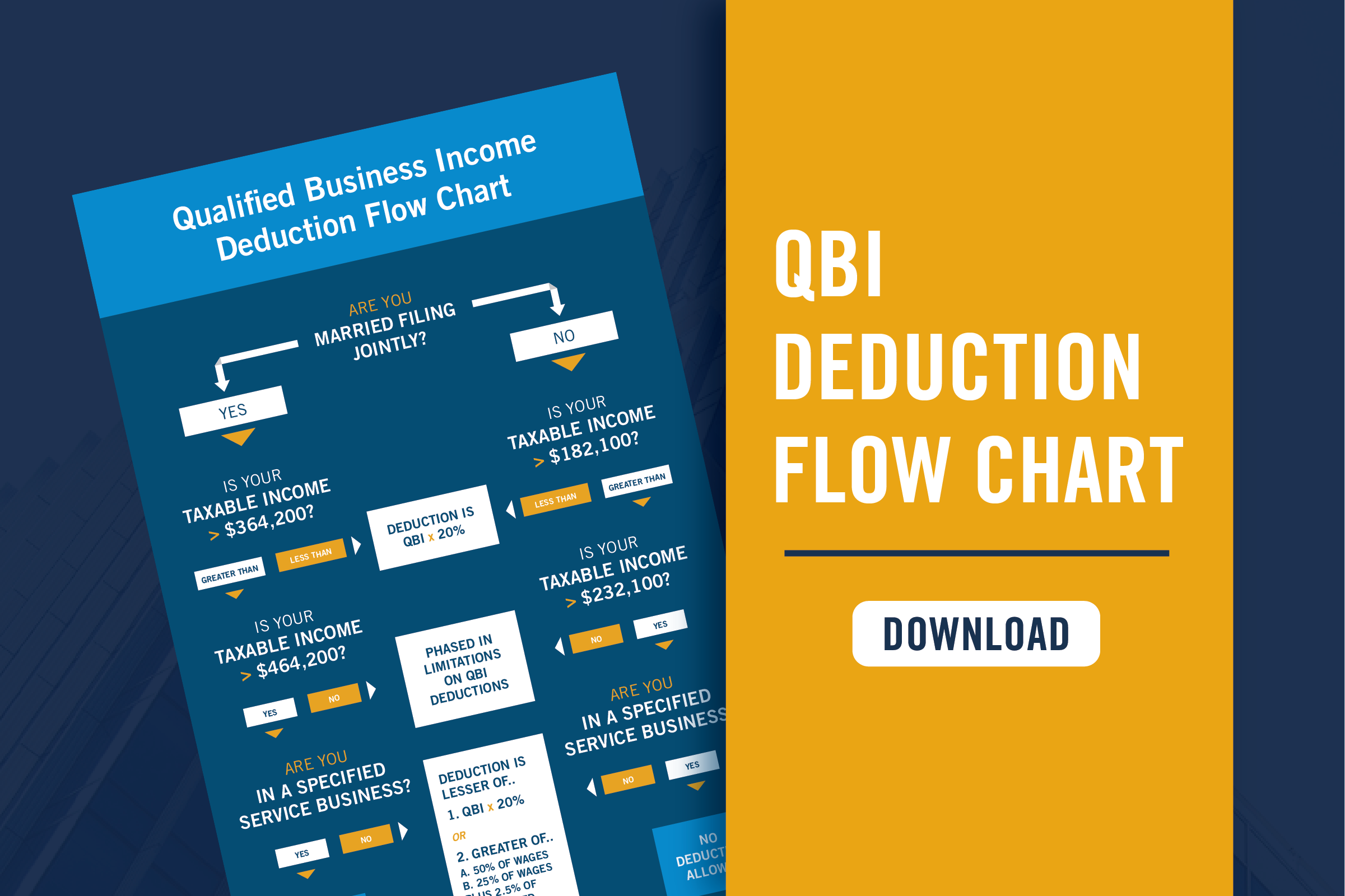
Security Implications of a Remote Work Environment
- Contributors
- David Mills
- Tyler Mills
Oct 3, 2023
The shift for many to a remote or hybrid work environment has reshaped the landscape of traditional office settings. As businesses adapt to this change, several advantages and challenges emerge. One significant concern is re-evaluating IT security risks in the context of remote work.
When evaluating risks in a remote environment and establishing protocols to minimize associated threats, it’s helpful to approach the issue from three separate angles: physical security, computer security, and connection security.
Physical Security
Keeping private data safe requires common sense and simple precautions as well as tech-based solutions. Remote workers should select a work site that offers adequate privacy. That means avoiding high-traffic areas such as the local Starbucks. Similarly, employees should delineate their workspace at home by keeping work computers for their own use rather than letting others share.
All employees should enable the automatic lock screen function on their device, so unauthorized users can’t access the system through a computer that’s logged in but unattended, however briefly. In the event of malware infection, workers should also know how to disconnect completely from the internet.
It is possible for a bad actor to come between the user and the application on the open internet. This is a security risk, especially on public Wi-Fi such as the free connections at coffee shops and hotels. Most companies have a virtual private network (VPN) that allows remote workers to connect with their office computer virtually, but this isn’t the case at every business — or for every type of work, even when the organization does have a VPN. Employees should use a personal VPN in these situations.
Computer Security
Working remotely requires a wide range of digital applications, including virtual meeting applications. Zoom gained immediate popularity as workers stopped coming into the office, but keep in mind that the free version does not allow for end-to-end encryption of web traffic.
GoToMeeting is an alternative that does use end-to-end encryption. Users must have a unique meeting ID to join a video conference, which eliminates the Zoom bombing phenomenon. The recently upgraded Google Hangouts is another fairly secure option for routine video conferencing.
Diligence in running updates is imperative for all applications. Employees need to understand the importance of installing updates as soon as they are available, whether on a company-issued machine or a personal device.
It’s also crucial for business leaders to make sure employees understand their legal obligations related to sensitive data. Healthcare data in particular demands adherence to a strict set of rules and regulations, and the consequences to the company can be severe in the event of a data breach.
Businesses that handle sensitive data of any kind should ensure that all who encounter the information take adequate precautions. It can be especially important to communicate this need to workers such as bank tellers, medical billers, and other administrative workers who may not have as much direct knowledge of the legal ramifications should an event occur.
Connection Security
Traditional IT controls are centralized, giving employers lots of control over what employees and their computers can do when they are connected to the network. However, maintaining that control is harder when workers are at home. At smaller entities that lack substantial in-house IT resources, it may be practically impossible.
Remote terminal services offer a relatively straightforward workaround. When workers log in through such a service, they are remotely connecting to the computer at the office, meaning standard controls are in place.
Most small and medium-sized organizations are opting for this strategy during the pandemic, but other methods exist. Some VPN providers can review certain components of an employee’s personal computer to make sure it is secure enough for safe connection to the VPN.
It is also possible to design infrastructure that lets staff remotely log in to the organization’s domain, though implementation is quite expensive. Due to the high cost, this strategy is probably not a viable near-term solution unless the infrastructure is already in place.
Incident Response Procedures
Management should clearly establish — and effectively communicate — incident response procedures before employees begin working from home. While this information is most relevant to computer security, policies and procedures should also cover incidents related to physical and connection security. In addition to providing written guidelines, leaders should:
- Test remote workers to verify they know what to do following any type of security incident.
- Provide ongoing training and testing to make sure knowledge of policies and procedures is complete and current.
- Define the steps for supervisors and managers to follow if they receive an incident report. This could include an in-person meeting at the office, depending on the severity of the incident.
The Critical Element: Empowered Users
Ultimately, the key to creating a secure remote work environment lies in empowering end users to make smart choices. Hardware and software solutions that maintain centralized control have their role, but true security exists only when users have both the tools and the knowledge they need.
The shift from in-office to remote work demands attention from company leaders to minimize new and traditional risks. Establishing appropriate, effective controls may demand significant resources and creativity. The payoff, however, is an organization that can operate more efficiently and securely in the workplace of tomorrow. Contact CRI for a risk assessment and help establish comprehensive internal controls suitable for a remote (or partially remote) work environment.